Backgrounds and Previous Researches
In recent years, with the progress of micro sensors and embedded systems, it is desired to provide services which components are associated with each other. We call the system composed of elements which can autonomously perform decision-making as Multi-Agent System (MAS). We call each constituent element in MAS as Agent, and the behavior of the entire system is given by the activity that networked agents are influenced by each other. From the perspective of Control Engineering, it has been discussed the way of the cooperative control in MAS[1]. Above all, the consensus problem which argues convergence of every agentユs state value is one of the well known problem[2].In order to introduce communication network, we have to consider the security. In other words, we must maintain services normally even if there are attacks for the network. In this paper, the term ``communication" refers to getting state values from neighbors. Attacks to the network can be classified as either deception attacks or Denial-of-Service (DoS) attacks. The former affect the reliability of data by manipulating the packets transmitted over the links. See references[3],[4],[5]. In this paper, we apply the latter attack pattern, DoS attack. In general, DoS attack means that the web server becomes unavailable by excess load[6]. While in this paper, DoS attacks affect by links wholly, or respectively, and no information can be transmitted through links affected by attacks.There are many previous works about the consensus problem under DoS attack. For linear systems, many results are revealed byet al.,[7],[8],[9],[10],[11],[12]. Specifically, we focus on[10]. In this literature, the class of DoS attacks are given by the assumptions about duration, and frequency. At each sampling time, if communication is not possible by the attack, the control input is given by zero. Thus, to solve the consensus problem, systems have to persist communication.A significance result in the prior research is the formulation of DoS attacks and the system's evolution. However, we consider the class of attacks can be more relaxed by the other protocol deciding sampling times. Specifically, we don't assume the frequency of attacks.To sum up, our basic question is, how to formulate system protocols under DoS attacks which is not necessarily satisfied with the assumption about frequency. For that purpose, we introduce stochastic protocols deciding sampling times.
Proposed Consensus Protocols
We consider the sampling times as random variables. That is, every sampling time is selected uniform randomly by the intervals which have the same length. In regards to the attack patterns, we consider three cases: the network-based attack, the edge-based attack, and the attack changing attack strategy. We prove that, for every attack cases we consider, consensus can be achieved using sampling times which are determined as above. For the network-based attack, Numerical examples are given as follows.
 |
| 図1: The graph structure |
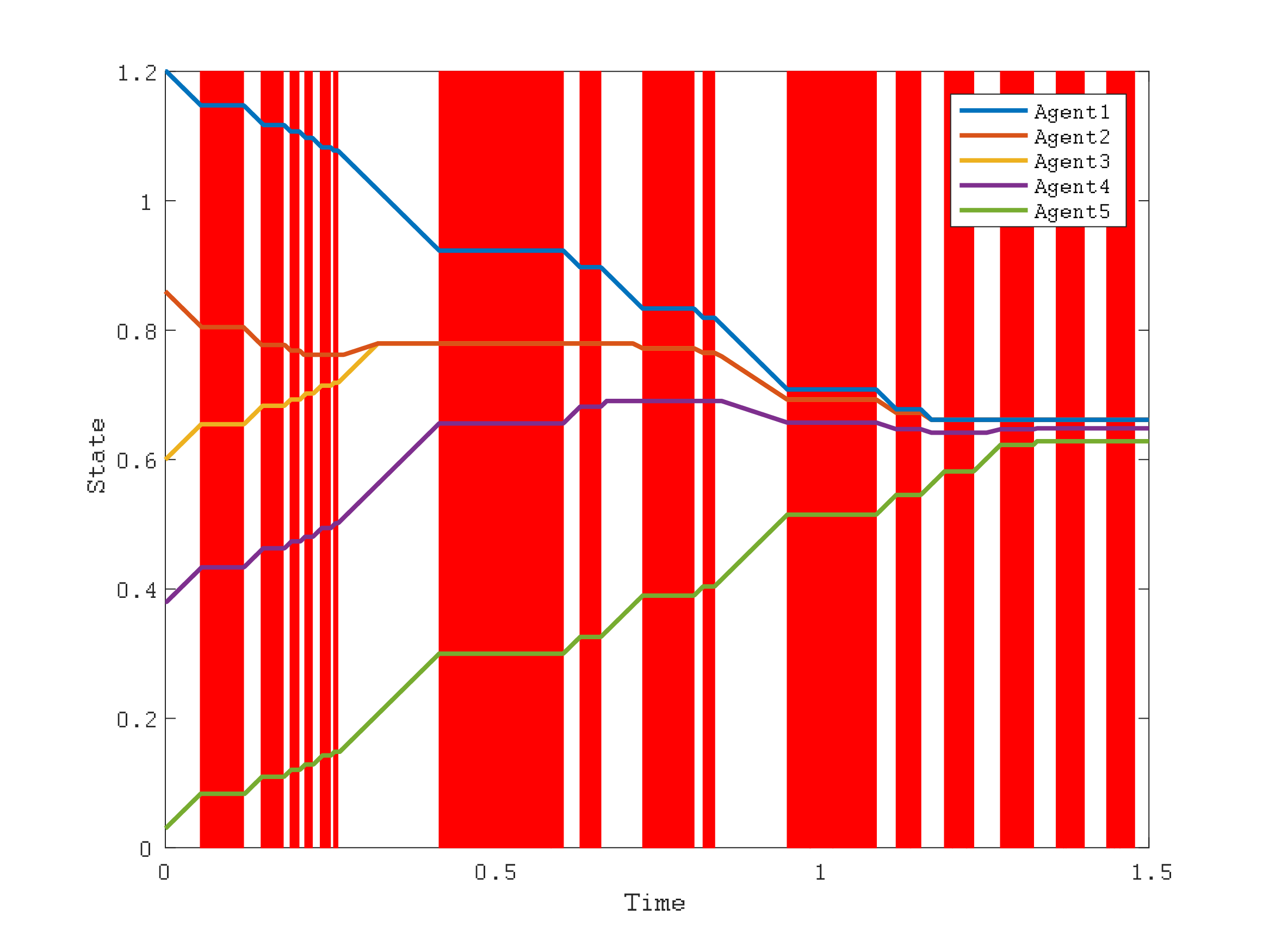 |
| 図2: The evolution of states under DoS attacks |
Conclusion
We investigate the consensus problem under DoS attack which is not necessarily satisfied with the assumption about frequency. As a result, for any attacks we assumed, we can propose the protocols which archive the consensus. However, we don't consider the performance of protocols, to be more specific, the convergence time of the system. If the time cost can be estimated, we can consider the attack trying to delay the convergence time. Moreover, we can consider the edge-based attack trying to manipulate converged state value. These extension are issues in the future.
Bibliography
[1] J. A. Fax and R. M. Murray, "Information flow and cooperative control of vehicle formations," IEEE transactions on Automatic Control, vol. 49, pp. 1465-1476, Sept 2004.
[2] R. Olfati-Saber and R. M. Murray, "Consensus Problems in networks of agents with switching topology and time-delays," IEEE Transactions on Automatic Control, vol. 49, pp. 1520-1533, Sept 2004.
[3] H. Fawzi, P. Tabuada and S. Diggavi, "Secure state-estimation for dynamical systems under active adversaries," 2011 49th Annual Allerton Conference on Communication, Control, and Computing (Allerton), pp. 337-344, Sept 2011.
[4] A. Teixeira, K. C. Sou, H. Sandberg and K. H. Johansson, "Secure Control Systems: A Quantitative Risk Management Approach," IEEE Control Systems, vol. 35, pp. 24-45, Feb 2015.
[5] F. Pasqualetti, F. Dorfler and F. Bullo, "Control-Theoretic Methods for Cyberphysical Security: Geometric Principles for Optimal Cross-Layer Resilient Control Systems," IEEE Control Systems, vol. 35, pp. 110-127, Feb 2015.
[6] J. Bellardo and S. Savage, "802.11 Denial-of-service Attacks: Real Vulnerabilities and Practical Solutions," Proceedings of the 12th Conference on USENIX Security Symposium - Volume 12, pp. 2-2, 2003.
[7] C. De Persis and P. Frasca, "Robust Self-Triggered Coordination With Ternary Controllers," IEEE Transactions on Automatic Control, vol. 58, pp. 3024-3038, Dec 2013.
[8] C. De Persis, "On self-triggered synchronization of linear systems," IFAC Proceedings Volumes, vol. 46, no. 27, pp. 247-252, 2013.
[9] C. De Persis and P. Tesi, "Input-to-State Stabilizing Control Under Denial-of-Service," IEEE Transactions on Automatic Control, vol. 60, pp. 2930-2944, Nov 2015.
[10] D. Senejohnny, P. Tesi and C. De Persis, "Self-triggered coordination over a shared network under Denial-of-Service," 2015 54th IEEE Conference on Decision and Control (CDC), pp. 3469-3474, Dec 2015.
[11] D. Senejohnny, P. Tesi and C. De Persis, "A Jamming-resilient Algorithm for Self-triggered Network," arXiv preprint arXiv:1603.02563, 2016.
[12] D. Senejohnny, P. Tesi and C. De Persis, "Resilient self-triggered network synchronization," 2016 IEEE 55th Conference on Decision and Control (CDC), pp. 489-494, Dec 2016.